First Collaborative Discussion Summary: Cryptographic Failures
In 2021, cryptographic failures were listed as the second most important security risk in web applications out of a total of ten security risks identified by the OWASP (Owasp, 2021). Current encryption algorithms provide reasonable security. However, vulnerabilities still exist and arise due to different reasons. They can be grouped into main four reasons.
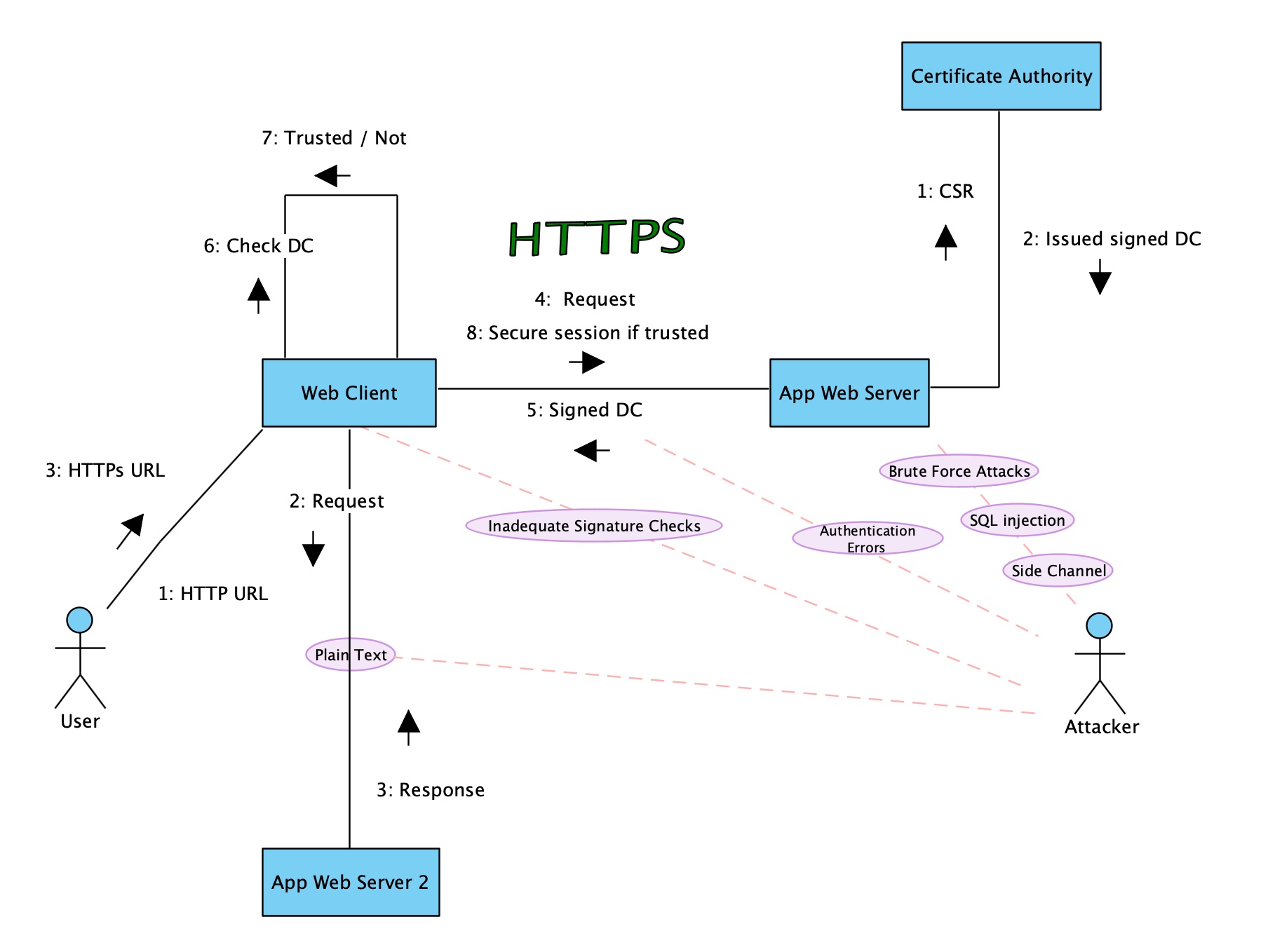
The first one is due to the use of plain text to communicate sensitive data (Lazar et al., 2014; Wagnon, 2022). This provides a straightforward method for network sniffers to obtain data.
The second one is due to a group of problems that give access to an attacker, i.e., a man-in-the-middle, to communicated data. This includes authentication errors and inadequate checks of digital certificate signatures (Lazar et al., 2014). Authentication errors may happen because of software bugs like the “Go to” bug in Apple operating systems that led to approving invalid signatures (Lazar et al., 2014; Cve, 2013). This means that authentication errors might happen due to programming faults and have serious consequences. Also, inadequate or inexistent signature checks might happen due to software bugs. An example of this is an android application that didn’t verify x.509 certificates from SSL servers (Cve, 2014). The two examples will eventually allow the attacker to spoof servers with crafted certificates to gain access to the web applications.
The third one is brute force attacks that succeed due to all sorts of weaknesses in the encryption process, which include, low encryption strength, weak encryption keys, insufficient randomness during key generation, the use of outdated encryption algorithms, and incorrect use of encryption libraries. These allow attackers to break cryptography by guessing (Lazar et al., 2014; Yousef, 2017).
The last reason is due to side-channel attacks which summarize indirect ways of breaking cryptography like timing attacks. This timing attack is performed by calculating the time spent during cryptogamic processes (Kocher, 1996).
It is worth mentioning that a study that explored the sources of cryptographic failures found that 83% of the vulnerabilities are caused by incorrect use of cryptographic libraries and not due to problems in the libraries themselves (Lazar et al., 2014).
To represent the reasons for cryptographic failures, a UML communication diagram was chosen due to its ability to show interactions between objects through messages. This allows the depiction of the communication that happens in the client-server architecture including the certificate authority. This was designed using Visual Paradigm Community Edition (Version 16.3).
References
Cve (2013) CVE - CVE-2014-0092. Available from: https://cve.mitre.org/cgi-bin/cvename.cgi?name=cve-2014-0092 [Accessed].
Cve (2014) CVE - CVE-2014-1967. Available from: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1967 [Accessed].
Kocher, P. C. (1996) ‘Timing Attacks on Implementations of Diffie-Hellman, RSA, DSS, and Other Systems’. Advances in Cryptology — CRYPTO ’96, 16th Annual International Cryptology Conference, 18-22 August 1996 Santa Barbara, California, USA. Springer.
Lazar, D., Chen, H., Wang, X. & Zeldovich, N. (2014) ‘Why does cryptographic software fail’. Proceedings of 5th Asia-Pacific Workshop on Systems, 2014 Beijing, China. ACM, 7.
Owasp (2021) OWASP Top Ten. Available from: https://owasp.org/www-project-top-ten/ [Accessed June 25 2022].
Wagnon, J. (2022) 2021 OWASP Top Ten: Cryptographic Failures. Available from: https://www.youtube.com/watch?v=2CMNNAJ6Ixc [Accessed June 25 2022].
Yousef, N. (2017) The many, many ways that cryptographic software can fail. Available from: https://www.freecodecamp.org/news/why-does-cryptographic-software-fail-often-d660d3cdfdc5/ [Accessed June 23 2022].
Seminar 1 Blog Post: Internal Threats
There are several external sources of threats that endanger the information security of companies. However, attacks by internal individuals of the company are not less important and are often more harmful than external ones (Newcombe, 2012; Upton & Creese, 2014). Several factors lie beyond that, some of which were revealed in an international research project that aimed at detecting internal threats and finding solutions to those threats (Upton & Creese, 2014).
One of the most important factors of the increased danger of internal attacks is the privileged access provided for company employees and the greater range of attack possibilities. Another factor is the use of own devices which may bring the risk of infection with viruses and malware. In addition, the careless use of the web and social media at work can threaten information security through scams and phishing. Furthermore, the possible communication between employees and service companies with which outsourcing contracts are established could lead to a security threat (Upton & Creese, 2014).
Several solutions are available. The first one is the adoption of a strong internal policy detailing what practices to be avoided by employees, the consequences expected in case of an event, and the correction steps that need to be done after an event. This policy should be supported by education. The second one is by enhancing the knowledge about, and the preparedness for possible attacks, and the understanding of the importance of reporting suspicious behaviors through education and training. The third one starts from the time of hiring by performing background checks, asking interview questions tailored to reveal internal values, and assessing the security awareness of candidates. Other solutions are in form of reviewing access control lists, monitoring the network activity of employees, and the use of malware-detection software and internal threat detection systems (Upton & Creese, 2014; Pillai, 2017).
Tutor's feedback
Dear Mohammad, I really like how you have built into your discussion the risk of BYOD - this is an effective idea in relation to threats coming from the inside. I also like your consideration of the background checks at the stage of interview, helping to bring people into the organisation only who are credible and trustworthy. I believe that these are both important steps for an organisation to take when working towards achieving security. A very nicely written post, Mohammad, well done. Cathryn
References
Newcombe,
L. E. E. (2012) SECURITY THREATS
ASSOCIATED WITH CLOUD COMPUTING. IT Governance
Publishing.
Available from: http://0-www-jstor-org.serlib0.essex.ac.uk/stable/j.ctt5hh6g0.9.
Pillai, A.B.(2017) Software Architecture with Python.Available from: http://0-search.ebscohost.com.serlib0.essex.ac.uk/login.aspx?direct=true&db=nlebk&AN=1513359&site=eds-live.
Upton, D. M. & Creese, S. (2014) The Danger from Within. Available from: https://hbr.org/2014/09/the-danger-from-within [Accessed September 2014].
Team Discussion: What is a Secure Programming Language
You should read Chapter 2,6,7,8 of the course text (Pillai, 2017) and Cifuentes & Bierman (2019) and then answer the questions below, adding them as evidence to your e-portfolio.
- What factors determine whether a programming language is secure or not?
- Could Python be classed as a secure language? Justify your answer.
- Python would be a better language to create operating systems than C. Discuss.
Team component
You should discuss your answers within your team, and you can share your team responses with the tutor for formative feedback or discuss it in next week’s seminar.
QUESTION 1
A programming language can be considered secure if it can “provide first-language support to address the causes for the most common, significant vulnerabilities found in real-world software” (Cifuentes and Bierman, 2019).
Some of the vulnerabilities that a secure programming language should prevent are the buffer overflows, SQL injections, cross-site scripting (XSS), OS command injections, and information leaks. Also, an interesting finding in one of the studies that explored the sources of cryptographic failures was that 83% of the vulnerabilities were caused by incorrect use of the cryptographic libraries and not due to problems in the libraries themselves. So an important factor in making a secure programming language would be to have resistance to developers' critical mistakes (Lazar et al., 2014).
The analysis conducted by Cifuentes and Bierman revealed that none of the mainstream languages address all the three main exploited vulnerabilities.
QUESTION 2
Python, like any other mainstream languages, presents a series of vulnerabilities. Pillai, A. B. (2017) explored a series of security issues affecting Python such as overflow errors, serialization issues and reading and evaluating input. Moreover, Pillai provided a set of examples on how the language is vulnerable in web applications and how it can be subject to certain attacks such as XXS, DoS and SSTI. These attacks can be mitigated with the solutions adopted by Pillai in his examples.
Python, like all other programming languages, is not considered natively secure as concluded by Cifuentes & Bierman (2019) and indirectly by Pillai (2017). By carefully applying certain secure coding strategies, secure software systems can be developed by using Python.
QUESTION 3
Both languages can be used to write an operating system but Python can not write a full operation system because it is an interpreted language and has limitations to write instructions for the hardware (History-computer.com, 2022). Also, managing memory is still an issue that can’t be addressed adequately for an operating system using Python (Cifuentes and Bierman, 2019).
Python is a very high-level language (VHLL). This means that Python uses a higher level of abstraction, conceptually further from the underlying machine, than do classic compiled languages such as C, C++, and Fortran, which are traditionally called “high-level languages” (Martelli, et al., 2017).
References
Cifuentes, C. and Bierman, G. (2019). What is a Secure Programming Language? DOI:10.4230/LIPIcs.SNAPL.2019.3.
History-computer.com (2022). C vs Python: Compared. [online] History Computer. Available from:https://history-computer.com/c-vs-python/ [Accessed 2 Jul. 2022].
Lazar, D., Chen, H., Wang, X. & Zeldovich, N. (2014) ‘Why does cryptographic software fail’. Proceedings of 5th Asia-Pacific Workshop on Systems, 2014 Beijing, China. ACM, 7.
Pillai, A.B. (2017) Software Architecture with Python. Birmingham, UK: Packt Publishing. Available from:https://search.ebscohost.com/login.aspx?direct=true&AuthType=sso&db=nlebk&AN=1513359&site=eds-live[Accessed: 1 July 2022].
Martelli, A., Ravenscroft, A. & Holden, S. (2017) Python in a Nutshell : A Desktop Quick Reference. Sebastopol: O'Reilly Media, Incorporated.